Crypter Cracked Egg
Ads for various crypting services. This hardly comes as news for anyone in the security industry who’s been paying attention over the past few years, but I’m writing about it because this is a great example of how the cybercrime underground responds to — and in some cases surpasses — innovations put in place by the good guys. About 15 years ago, when the antivirus industry was quite young, there were far fewer competitors in the anti-malware space. Most antivirus firms at the time had a couple of guys in the lab whose job it was to dissect, poke and prod at the new crimeware specimens. After that, they’d typically write reports about the new threats, and then ship “detection signatures” that would ostensibly protect customers that hadn’t already been compromised by the new nasties. This seemed to work for while, until the smart guys in the industry started noticing that the volume of malicious software being released on the Internet each year was growing at fairly steady clip.
Many of the industry’s leaders decided that if they didn’t invest heavily in technologies and approaches that could help automate the detection and classification of new malware threats, that they were going to lose this digital arms race. So that’s exactly what these firms did: They went on a buying spree and purchased companies and technologies left and right, all in a bid to build this quasi-artificial intelligence they called “heuristic detection.” And for a while after that, the threat from the daily glut of malware seemed to be coming under control. But the bad guys didn’t exactly take this innovation laying down; rather, they responded with their own innovations. What they came up with is known as the “crypting” service, a service that has spawned an entire industry that I would argue is one of the most bustling and lucrative in the cybercrime underground today.
EggCrack P1,ativador manicraft,manicraft,como ativar manicraft,craker manicraft,Minecraft Cracker,Babylon RAT v1.6.0.0 Cracked,curso,ebook,hacker,hacking,anonymous.

Put simply, a crypting service takes a bad guy’s piece of malware and scans it against all of the available antivirus tools on the market today — to see how many of them detect the code as malicious. The service then runs some custom encryption routines to obfuscate the malware so that it hardly resembles the piece of code that was detected as bad by most of the tools out there. And it repeats this scanning and crypting process in an iterative fashion until the malware is found to be completely undetectable by all of the antivirus tools on the market. Incidentally, the bad guys call this state “fully un-detectable,” or “FUD” for short, an acronym that I’ve always found ironic and amusing given the rampant FUD (more commonly known in the security industry as “fear, uncertainty and doubt”) churned out by so many security firms about the sophistication of the threats today. In some of the most sophisticated operations, this crypting process happens an entirely automated fashion (the is a great example of this): The bad guy has a malware distribution server or servers, and he signs up with a crypting service.
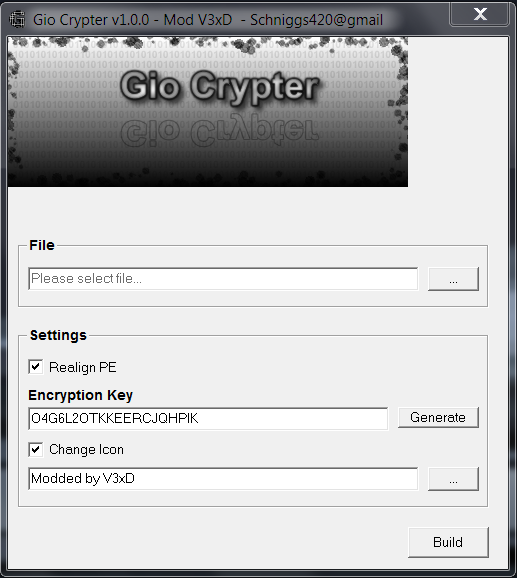
The crypting service has an automated bot that at some interval determined by the customer grabs the code from the customer’s malware distribution server and then does its thing on it. After the malware is declared FUD by the crypting service, the bot deposits the fully crypted malware back on the bad guy’s distribution server, and then sends an instant message to the customer stating that the malware is ready for prime time.
Crypting services are the primary reason that if you or someone within your organization is unfortunate enough to have opened a malware-laced attachment in an email in the first 12-24 hours after the bad guys blast it out in a spam run, there is an excellent chance that whatever antivirus tool you or your company relies upon will not detect this specimen as malicious. In short, as I’ve noted time and again, if you are counting on your antivirus to save you or your co-workers from the latest threats, you may be in for a rude awakening down the road. Does this mean antivirus software is completely useless? Very often, your antivirus product will detect a new variant as something akin to a threat it has seen in the past. Perhaps the bad guys targeting you or your organization in this case didn’t use a crypting service, or maybe that service wasn’t any good to begin with.
In either case, antivirus remains a useful — if somewhat antiquated and ineffective — approach to security. Veronika Decides To Die Pdf Download Free on this page. Security is all about layers, and not depending on any one technology or approach to detect or save you from the latest threats.
The most important layer in that security defense? Most threats succeed because they take advantage of human weaknesses (laziness, apathy, ignorance, etc.), and less because of their sophistication. So, take a few minutes to browse, and my. Oh, and check out the Wall Street Journal piece that prompted this rant,. Sometimes you hide your code to prevent other people from stealing from you. It’s not a perfect solution to protecting intellectual property, and i certainly wouldn’t endorse it, but i know that some people do use this technique.
I’ve even heard of a crypting product years ago that used the same algorithm (MtE) that a virus writer named Dark Avenger created and used in his viruses. Alan Solomon told me the legal ramifications of false alarming on legit binaries encrypted with that algorithm was what kept Dr Solomons Anti-Virus from simply alerting on the the MtE engine itself in order to catch all the malware that used it. I’m not worried about a few software devs having some issues; using crypter-like methods to “hide” your code is a lot like walking into a convenience store wearing a ski mask; don’t be surprised when the police or “overzealous” police suddenly show up to escort you to the quarantine folder. The developers would simply have to adapt in their ways, once enough security applications have adopted the technique.
I think users will hate you more, if you fail to catch malware, because you gave a free pass to software trying to conceal its purpose. A former employee of Symantec – and Trend Micro, and of other security companies, I can tell you that the better AV products stopped relying on file scanning as the primary means of protection years ago. The better solutions – BitDefender, Kaspersky, Symantec (Norton), and others all provide layers of protection. The free av products typically rely on file scanning. The suites also include file reputation (has that file been seen before and is is assocated in with malicious type behavior), source reputation, heauristics, IPS, traffic monitoring. The point is that the phrase “AV is dead” is meaningless – as are those AV tests that only look at file scanning.
What the security industry really needs is a well funded, independent source of efficacy tests. Most of the efficacy testing is paid for by the vendors – and testing this stuff is very expensive. I used to help manage some of the competitive testing at an AV company – so I know how they stack the deck.
The magazines that review these products long ago stopped doing independent testing. There are big differences in detection rates between security products – good luck trying to find the data. That’s not new, that’s called whitelisting. Many AV vendors provide whitelisting functionality these days.
That being said, it’s not easier than compiling a list of all the bad software out there, it’s actually much harder for 2 reasons: 1) there are orders of magnitude more good binaries than bad, and the number of good binaries is increasing orders of magnitude faster than the bad ones (see here ) 2) the only criteria we have for declaring something is good is that we can’t find anything bad in it, so we’re still left with looking for the bad things, even when compiling a list of good things. I have Windows Parental Control application white list turned on my honey pot – it does pretty well.
It only worries about the executables already on the machine; any thing new tries to run, it gets squashed. It seems to work very well, and I still have good functionality. If I have something I need to run, I allow it in the administrative account. Of course there is always the UAC also.
I find that a good HIPs goes a long way too. I’m beginning to think that is almost all Emisoft uses on their anti-malware product. Anti-virus is dead – long live the anti-malware! You’re right, and I’m not surprised.
Really, whitelisting’s best use is in cases where a workstation’s – or server’s – functionality is strictly defined, and only certain executables are ever supposed to run with few to no exceptions. That’s way more often the case with corporate/enterprise systems, and very rarely so with general use home systems. Too much general functionality is demanded of home computers and mobile devices to make whitelisting truly practical. So while it’s attractive, it ends up being so blasted time consuming that it drives an end-user crazy. And risks having them relax security in order to end the aggravations.
It has its positives, but all I have to think about is making my mother, or various aunts implement this and I can see what a support burden it would be. I’ve often liked the idea behind Tripwire i.e. Create a baseline hash of executable and monitored files when in a known safe, not-compromised state, then regularly rerun those hashes and see what’s changed, then flag it for examination. Problem is, on the individual workstation level that’s even more time-consuming than straight-out whitelisting, and will often give tons of false positives. Enterprise Tripwire would of course have automation tools, but that’s too big a cost to the end user, not to mention too big a burden. I don’t know what the solution is.
I’ve heard many suggestions converging on cloud computing and eventually virtualizing the entire user profile and desktop experience, but I’m sort of wary about those ideas. I just don’t know how to solve the problem. My whitelisting approach isn’t too difficult. Stuff is whitelisted by where it’s located in the filesystem. If it’s located where only an elevated Admin could put it, then it is allowed.
Non-Admins or unelevated Admins can use what’s in those locations, but they (or something exploiting their limited powers) cannot put new stuff where execution is allowed* Anything that colors outside those lines is arbitrarily denied. Is it perfect? Some software is *designed* to color outside the lines. The Steam game client and the consumer version of Google Chrome are a couple offenders. Definitely power-user territory for the home user. As you move across the spectrum from home to SOHO to SMB to enterprise, I think it gets more practical.
This does assume the Admin rights are in trustworthy hands to start with, but if they’re not, you’re sunk regardless. *unless it can pull off a privilege escalation or a social-engineering technique to trick them into elevating.
But that would never happen, no sir 😉. And who’s going to pay to test every build of every piece of software for every OS for every architecture out there? There goes the open source movement and, therefore, the internet. And all small companies and start ups.
Hell, I doubt even the big companies would be able to afford it. Innovation would die. Profit margins would dive.
Many of them won’t shell out for existing AV products; no-one’s going to pay enough to cover even the bureaucratic cost of scanning very piece of software used, let alone cover the cost of the actual scanning process. And if it was done, what would happen? The bad guys would start writing nice little free utilities that turned bad a few weeks later. How do you test software that parses rulesets? That exhibits odd bugs in certain circumstances? We fail to find bugs when software has been written with the best intentions, we have no hope of finding bugs that have been deliberately, discretely added. Brian, in your 3 Tips section, you mention Download.com.
Romanian Map Ets 2 Download Torent Gta. Have you ever tried to download something from that C NET site? OMG the site may have a legitimate app to download, but the ads mimic the download buttons too well. Like a magazine that feels it is immune from the ads it sells space to (aka income), I refrain from web sources that propogate and rather, visit the original creator’s home. I think C net needs a swift hit on their income to realize how they contribute to the issue of end-users getting taken. Even a saavy person will have to hesitate on d/l where the link isn’t what it appears. Adservers, and advertisers should also be held accountable for their “poorly” crafted ads and servers hosting them. And how some apps (say for iPhone) incorporate ads as an income source, some ads are so poorly designed or obnoxious that, the user will not take the product as “reliable”, “trustworthy” or effective.
Go the pay route or enlist the ads that aren’t headaches. Plus the news that in the future, Google doesn’t want any URL indicators? So we won’t know where we are? I can’t help but reply here, because that whole CBS takeover of CNET, ZDNet, and Tech Republic is a thorn in my side.
Because of their greed, they’ve practically ruined all of those formerly popular assets; I can’t log into most of their discussion because of all the attempted page redirects, and malicious ‘malvertisements’ my browser gets hit with when I lower the defenses so I can post over there. So it isn’t just the downloads that are a disaster, but the whole CBS family that is going down hill. It makes me very angry, because those sites used to be my favorite hang outs. It will just be a matter of time before the robber barons soak them for all they’re worth, and throw them into the garbage dump of history.
Brian – me and my friends who develops software protection technologies (aka exe-protectors, exe-packers, code virtualizers, license key systems) are innocent victims of those antivirus engines who tags anything suspicious as a potential virus (false positive detection). Software like PELock, Themida, VMprotect, Armadillo, Obsidium are used to protect legit software products against cracks, patches, keygens and all kind of nasty stuff from the hands of crackers. But when someone wants to use our products they usually find themselves in troubles because of the low quality antivirus products who tags protected software as a virus. I have lost many customers because they wouldn’t accept this to happen to their final products (imagine someone downloads their software and antivirus warning pops up – it’s a disaster for software maker), and there are so many antivirus products on the market it’s virtually impossible to cooperate even with a small number of their developers (I don’t even have to tell you it’s hard or even impossible to reach them and work out some solution). There’s a light at the end of this road called TAGGANT technology, but still I think many antivirus products are low quality and tags everything suspicious as a virus without any decent proof (hash, signature from the known malware, behavior analysis or anything that clearly would state it’s a malware). I think antivirus products works this way so they can earn more money from their customers, it’s always easier to tag something as a virus then properly analyze the file – it would require more work from the antivirus developers.
I’ve been working in the past for several antivirus companies and I know how they treat it – without much attention. One funny example – one antivirus company claimed they are supporting detection of my exe-protector (so they can scan the protected file content beneath the protection layer) but I didn’t even spoke to any of their developers and they didn’t even bought the license of my software – they either had to analyze a limited demo version of my protector or have used carded copies of my software released to the Internet. That’s how much they care 😉 PS. I don’t use any antivirus product – after my experiences I think it’s a garbage software that slows down entire PC, it cannot properly detect legit protection technologies and in the end can’t even protect against latest malware that is properly tested against antivirus products – so what’s the point of using something like that? The answer is simple – none 😉 You still don’t believe me? Read about Stuxnet – it wasn’t detected for months by any antivirus product until someone manually analyzed the thing and add detection signatures to the antivirus products. Do you think it’s different for other complex malware?
Most users go to CNET and read the user reviews on there. It would promote your product if you would submit it to download.com for dispersal. Your Armadillo has no user reviews even though it is available. I’ve always taught my clients to regard products with no reviews as suspicious, and to watch out for products with canned reviews that are obviously from spammers, or shills working for the company.
It is kind of a what comes first the chicken or the egg? I realize that, but that is the reality of new software in the market. You could always try File Hippo or majorgeeks, I’m not sure what it takes to get your software listed on those sites, but they are some the best! “Software like PELock, Themida, VMprotect, Armadillo, Obsidium are used to protect legit software products against cracks,” That may be the intention, however, they obscure the code, or include non-deterministic self-modifying code. They can obscure malicious behavior, and crackers still manage to defeat the “protections”, anyways.
I am not willing to use or recommend any software product that uses means to obscure the executable image and prevent or deter analysis of what the software does at a low level, when run on my CPU it is definitely not legitimate, even if the goal intended to be accomplished of deterring software piracy is legitimate: there is a problems with the means, that is: attempted concealment of the binary code being executed is never legitimate. “Read about Stuxnet – it wasn’t detected for months by any antivirus product until someone manually analyzed the thing and add detection signatures to the antivirus products.” What you have there is called an outlier; the vast majority of threats antimalware has to deal with are nothing like stuxnet. The detection rates for the AV-comparatives shown for Kapersky, Emsisoft, etc, are pretty compelling. Although at 99%, you are still expected to be infected after a few attacks, unless you combine multiple malware detection methodologies, including whitelisting, patching, and the use of exploit mitigation tools such as EMET and additional non-standard sandboxes (beyond protections the attacker will expect). I found this a really valuable post. It’s interesting that the WSJ writer didn’t bother to discuss the reasons why antivirus is dead as this post did.
He just threw it out there with no context. I think the issue is much bigger than just antivirus.
All signature based solutions face the same issues. For example WAF, IDS, etc that are based on signatures are also vulnerable to obfuscation attacks. I’ve watched dozens of YouTube videos on how to quickly walk around these devices.
Feels like there’s going to be a seismic shift in IT security strategies over the next couple of years as the industry moves away from signature-based technologies. As mentioned previously, the fact that an executable file is obfuscated or encrypted is in itself an indication of a suspicious file.
If there are also other suspicious indications (such as location on the computer, file size, detail registered with the operating system, an invalid digital signature, a bad file “envelope”, and other common sense indications, that adds more validity to the detection as malware. And this can be done without file parsing and complicated techniques like emulation or sandboxing. The AVs need to work smarter, not harder. It is interesting to observe the reaction in my honeypot for those attacks. I had Foxit installed – the attack failed – my HIPS grabbed it, and it was all over! Sometimes it is good to either use applications with fewer vulnerabilities, or at least keep the ones that do, updated the instant a patch comes out.
Auto updaters can help here – even if they can’t do the update, they can alert you to the patch. I’ve seen many attacks fail just running as a limited user, on a Windows machine running NT5 or 6, as long as the latest updates for everything installed is in force. To be honest, most av software will detect these crypted malware programs due to their so obvious methods of infection. AV software does not rely only on signatures, calls to the the kernel and other IO are all monitored and will result in at least a notification to the user from the av software in most cases. Layers of course, for companies that is easy, for personal computers at home, layers normally include a simple hardware router and firewall that may do inline scanning if its capable and then software on the OS. Adobe gets a bad rap, but they are decent at providing security patches and automatic updates. Also, with Chrome Flash can be sandboxed, mitigating much of the risk Oracle, JAVA on the other hand is an utter nightmare.
The security of Java has more holes than a block of swiss cheese. Updates to free Java come out very slowly, even when being exploited, and are often batched. Also, Java’s “automatic update” functionality” is obtrusive and not very good — they always seem to be trying to trick you into getting a new toolbar with every update and turning BACK ON the Java applets feature that you had manually disabled. Also, JAVA5 and JAVA6 are widely used. Many network devices and end user packaged products still require the versions of Java to be installed to manage network equipment, not compatible with JAVA7 or JAVA8.
Every 3 years, Oracle decides the previous version of free Java is “End of Life”, and stops making security updates for it — even though the vast majority of Java users are not free to upgrade, due to application incompatibility. No home user is going to pay Oracle 10 grande a year for security updates ergo, there are a lot of vulnerable Java versions running around that CANNOT be remediated. So Adobe is not the biggest ‘polluter’ here.
• Click Safari in the Menu Bar at the top of the screen, then Preferences. • Click the Privacy tab. • Under Website use of location services, click Prompt for each website once each day or Prompt for each website one time only. • MacOS may now prompt you to enable Location Services. If it does, follow its instructions to enable Location Services for Safari. • Close the Privacy menu and refresh the page. Try using Current Location search again.
If it works, great! If not, read on for more instructions. • Back in the Privacy dialog, Click Manage Website Data.
And type yelp.com into the search bar. • Click the yelp.com entry and click Remove. • You're good to go! Close the Settings tab, reload this Yelp page, and try your search again. If you're still having trouble, check out.
You can also search near a city, place, or address instead. I was slightly cranky when I arrived so being ignored for a good 10 minutes really got me peeved. I finally stopped a waitress that was flying around of I could just sit myself at the bar since I wasn't being seated. She explained the register runner was also to sit people, well that probably works fine if you don't have 4 groups waiting to cash out.
Anyways, after that frustration I had a wonderful breakfast. Good hash browns,with excellent eggs and I got to listen to the kitchen banter. My coffee cup never even got close to empty which earns a nice big tip. I've been trying to earn my Breakfast Club badge since FOREVER so naturally The Cracked Egg has been in my morning rotation. Nothing too fancy just your typical breakfast and brunch fare. Humble and welcoming vibe.
No judgement if you show up in your pjs (not that I ever would) but nice to know it doesn't really matter here. And even though the line looks long, you'll never have to wait longer than 20 minutes to be seated. I'm a creature of habit, so I prefer the omelettes and sub. With egg whites. The go-to, The Californian (of course). Anything topped with avocado and bacon is alright in my book.
The green omelette is a must try as well. Not a huge fan of the coffee cake (hard pass) mostly because I don't like sweets at breakfast. I want savory.
And a cup of coffee too so keep it comin'.;). We've come here many times and I get the same thing every time, what I specifically come here for.the cordon bleu skillet. It's amazing! They took it off the menu, but if you're going in looking for it and mention it to your server, you can still order it. My boyfriend has tried other meals and he's never had anything bad to say about any of them. If you are getting a meal that lets you choose between I think toast or the coffee cake, definitely choose the cake.
It's delicious!! You won't be disappointed.
It is sweet though so be prepared for that. They have different flavors throughout the year and they've all been really good. It does get really busy, especially on the weekends so make sure you plan ahead to wait a bit. On a positive note tho, even when the place was packed, after ordered, we got our food super fast. My friends and I decided to try this place out for breakfast. It was quite far from where we were staying in downtown, but still a pretty good place for breakfast. There was about a 10 minute wait, the place was pretty busy when we got there.
There were about 2 waitresses waiting on all tables. It took some time for someone to finally come to take our orders. We were waiting I'd say about 10 minutes or so.
We decided to order specials that was on the board. Overall taste of food was pretty good. We had Daisy's Benie and one other type of special, which I can't remember at the moment. Both were fully loaded and there was so much food on the plate including some fried potatoes and we couldn't finish our dishes. Daisy's Benie was tasted like a Mexican type dis and was full of flavor. I would definitely eat here again, yet try something new.
No matter which location you land at, its always packed which only exemplifies how popular they are. Especially on weekends. Especially after a Friday night party we threw at the house. Especially after a hangover! Nothing a hearty breakfast wont tame. I ordered the 'Big bad wolf' ( named after me of course! ) and the mrs.
Ordered the country benny. One thing i noticed is that they charge more for a small cup of coffee here than a venti Starbucks. You can opt for either toast or hot coffee cake. I took the coffee cake of course. No surprises with the food and the wait, even though they were very busy was only 10 minutes. The service here is A+. Another added bonus is that its only minutes from the casa.
If you make a habit of coming here every weekend, it will be a very expensive habit at $30 a pop. After your meal, you wait in line at the reception - cashier area which gets congested because its right next to the entry with a constant flow of people. They should have you pay at the table.
I've eaten here multiple times and I'm just now getting to write a review, lol. Depending on what time you come, this location tends to be pretty packed. I believe the longest I had to wait for seating was about 10 minutes, nothing more. The servers are always friendly and very attentive.
Also, food comes out in very good time. Coffee and water is constantly refilled. And paying at the end of the meal consists of going up to the register. The omelette or scramble choices here are pretty good. Do not ask for soft scramble! My eggs came out pretty runny when I asked for them not to be. But for next time, I know not to ask for soft, instead medium scramble.
The coffee cake here is to die for. I usually get a slice of it and it comes out nice and hot. They also have variations of the coffee cake from week to week. Is it my first breakfast place joint of choice? But it's definitely not my last. I came here on a Sunday morning for brunch. We sat outside since it was a nice warm day and thankfully, there were misters.
I got the Southwest Scramble and iced coffee. The portions here are big so I had trouble finishing my plate but it was delicious! Service was a little slow at times but they were busy that day. I just wish they'd have more people on the staff to check on people outside, as well. That being said, it was a great breakfast over all and I'd definitely come back to try more on the extensive menu:).
Came here on a Saturday morning, very busy. Expected the wait to be an 1 hour, but luckily for us, we were seated after waiting only 20 minutes. There was so much to choose from.
But I simply went with scrambled eggs turkey sausage and hash browns and wheat toast. The wait was about 15 minutes. I Requested my eggs scrambled medium. Let me first start off, my eggs were a bit still watery which threw me off. My turkey sausage was really dry, and I do wish my hash browns was cooked more, no crispness or browning on the hash brown.
It was a bit depressing. I still ate it all because I was hungry. Breakfast is so simple to cook, how could you not know how to hit all the right points on it. I'm not trying to be mean, probably it was just busy and it got hectic in the kitchen, sh*t happens. But if I'm ever in area, Id rather pass on this place. But the customer service was great!
The place is awesome tho. Looks like a big kitchen.